Azure AD FIDO2 Authentication
FIDO2 authentication is the latest method to sign in passwordless on devices and websites.
It was already possible for a few months to login passwordless with Microsoft accounts with a FIDO2 security key, but recently Azure AD FIDO2 authentication is in public preview.
In this blog I will show you how to setup your own tenant and device so you can leverage passwordless signin to Azure AD with FIDO2
Table of Contents
- What is FIDO2
- Downsides of passwords
- Benefits of FIDO2 (password-less)
- Requirements
- Enable combined registration preview
- Enable FIDO2 authentication
- User registration and management of security keys
- Login to websites with a FIDO2 security keys
- Login to Windows 10 with a FIDO2 security keys
What is FIDO2
FIDO stands for: Fast Identity Online
FIDO has been founded by the FIDO Alliance. The FIDO Alliance is an open industry association with a focused mission: authentication standards to help reduce the world’s over-reliance on passwords.
FIDO2 is the overarching term for FIDO Alliance’s newest set of specifications. FIDO2 enables users to leverage common devices to easily authenticate to online services in both mobile and desktop environments. The FIDO2 specifications are the World Wide Web Consortium’s (W3C) Web Authentication (WebAuthn) specification and FIDO Alliance’s corresponding Client-to-Authenticator Protocol (CTAP).
This makes it possible to login to services as Azure AD, or a random website, with a simple USB key, smartcard or even your phone.
This is based on the device that carries your credentials, combined with something you know or are. Like a PIN or a fingerprint
Downsides of passwords
Passwords are everywhere, because they are so simple to implement. But that simple implementation can also have it downsides!
Passwords are often reused
Because we need so many passwords, they are often recycled for different services. So when 1 password is compromised, multiple services are often at risk because the same password could be used for those as well.
Vulnerable to database hacks
Passwords are based on a pre-shared key. So the online service has a copy of your password, or a hashed version of your password.
These databases can be compromised, so an attacker can find out your password
Vulnerable to Brute Force attacks
Passwords need to be remembered, so are often easily breached by a brute force or dictionary attack.
Vulnerable to social engineering attacks
This could be a simple as watching over someone shoulder as he/she types the password, or by guessing the password based on data found on social media.
Vulnerable to keyloggers
Regular passwords are vulnerable for keyloggers, this could be a hardware based keylogger between the PC and keyboard, but also a software keylogger. These record all keystrokes, including your password
Benefits of FIDO2 (password-less)
With FIDO2 all downsides of passwords are non-existent. This is because of the following.
Public / private keys
FIDO2 does not use a pre-shared key, but it uses public / private key pairs.
The public key is handed to the identity provider (like Azure AD), and the private key stays on the device, and will never leave it. It will only be used to sign a challenge.
So even if your public key gets stolen it’s no problem, because it’s useless. That’s what makes it a public key after all.
Unique keypairs
Where passwords are often reused for different services, that isn’t the case with FIDO2. For every online identity a new key pair is generated. So every identity has its own public and private key.
Phishing is part of the past
Because your identity and keypair is linked to a login domain (like login.microsoft.com), a challenge from a phishing site won’t be recognized by your FIDO2 key. A phishing site will try to let your login to login.micr0s0ft.com for example, and your FIDO2 key won’t have a keypair for that login domain.
Social engineering
You will not be vulnerable to social engineering attacks, as there is nothing to guess. You don’t even know your own private key.
And if you use a FIDO2 key with a fingerprint there is also nothing to see when you login. So no more looking away for your colleagues.
Requirements
To enable FIDO2 authentication there are a few requirements.
- Enable combined registration (preview)
- Windows 10 1809 or higher met Microsoft Edge
- Compatible FIDO2 security key
For Windows sign in:
- Azure AD joined Windows 10 1809 or higher
Enable combined registration preview
The possibility to register a security key is only available in the new registration portal. That’s why we have to enable this feature first.
To to this login to https://portal.azure.com with a global administrator account. Go to User Settings -> Manage user feature preview settings
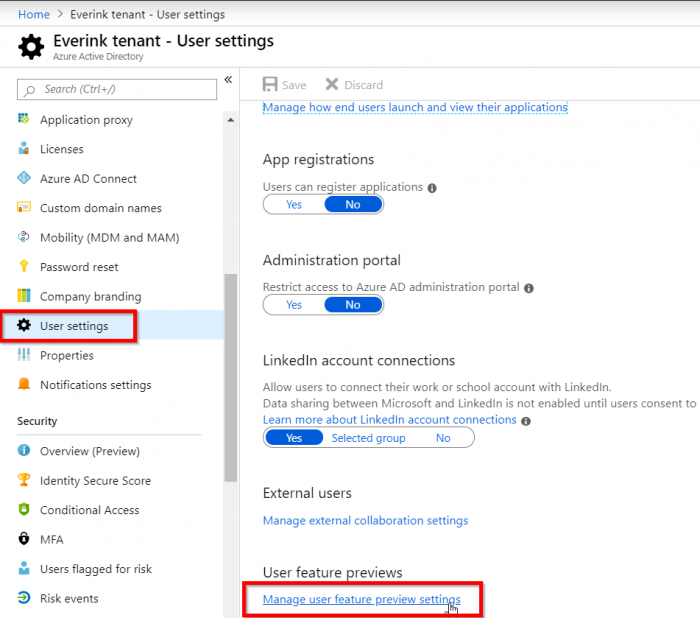
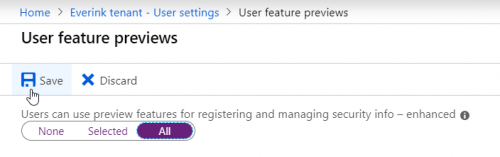
Make sure you select All or Selected for the feature:
- Users can use preview features for registering and managing security info – enhanced
If you choose Selected you can select a pilot group first. Then click on Save
Enable FIDO2 authentication
To enable FIDO2 as an authentication method we login to the azure portal with a global administrator account. Then go to Azure Active Directory -> Authentication Methods
Then click on FIDO2 Security Key
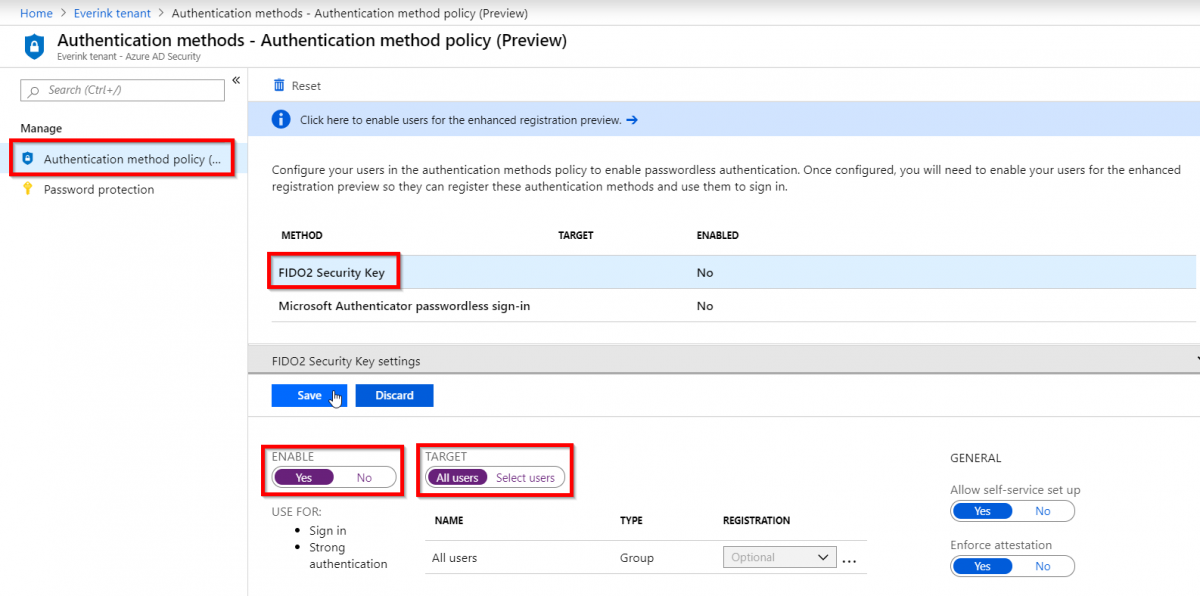
At ENABLE click Yes
At TARGET I selected All users. It is possible to select a pilot group or user here. Then click on Save
User registration and management of security keys
To register a security key as a user, you can go to the following page: http://aka.ms/setupsecurityinfo
Click on Add method
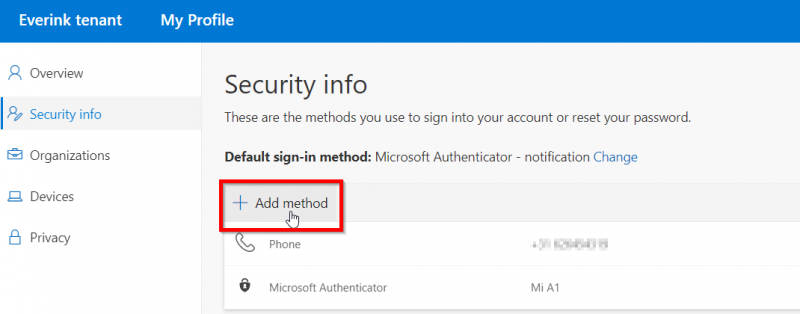
Then choose the option: Security Key and click on Add
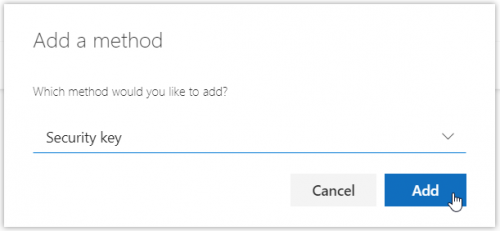
As my FIDO2 key is a USB device, I pick that.
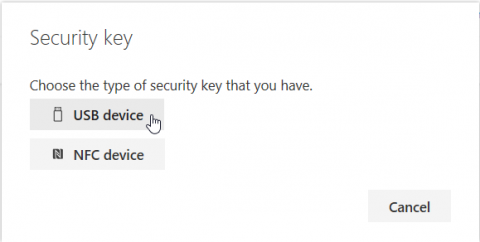
After that I have to take action on my security key. This is dependent on how your key is configured and which features it supports I have a Feitian Biopass with a fingerprint reader which is sufficient for me. Sometimes there’s only a single button on it, and you have to enter a PIN as additional verification.
You can also see that the public / private key pair will be made for login.microsoft.com, so the key pair will only work for this site.
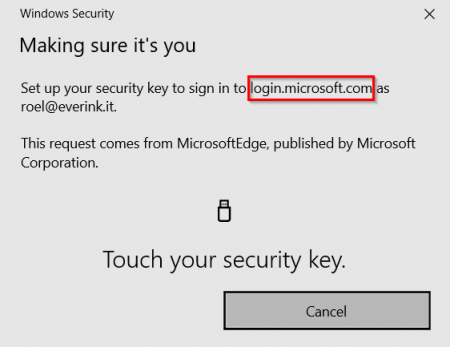
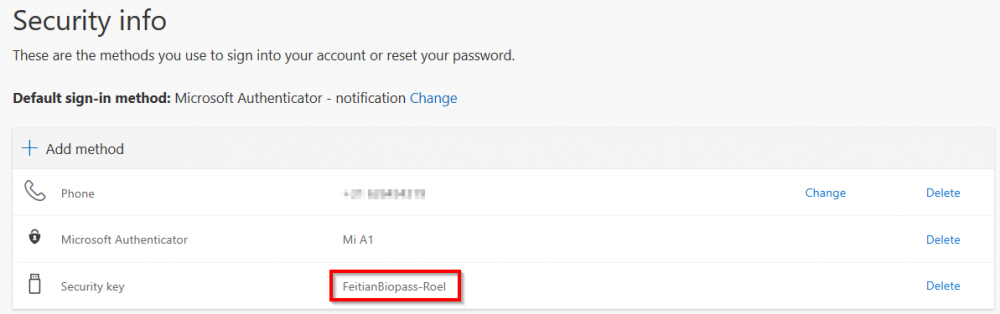
You can give your security key a descriptive name to identify it more easy. I call it: FeitianBiopass-Roel
Then the key is ready for use!
Login to websites with a FIDO2 security keys
To login to a website with our key we can go to any Microsoft page where we can login with our Azure AD account. Like https://myapps.micosoft.com, https://outlook.office.com, or https://office.com
Click on Sign-in options
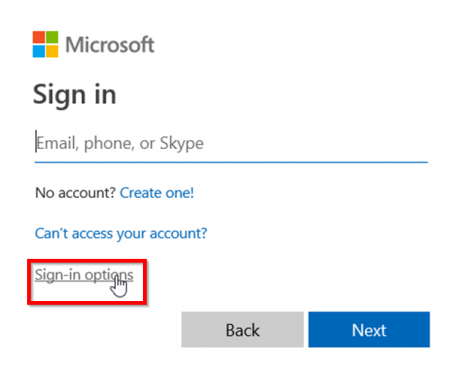
And then Sign in with a security key
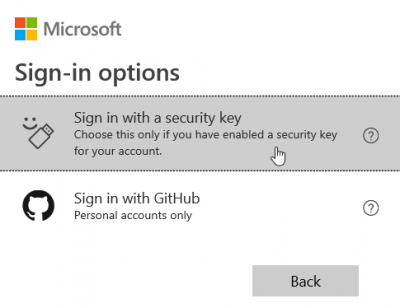
Then follow the instructions to insert your key, and take action.
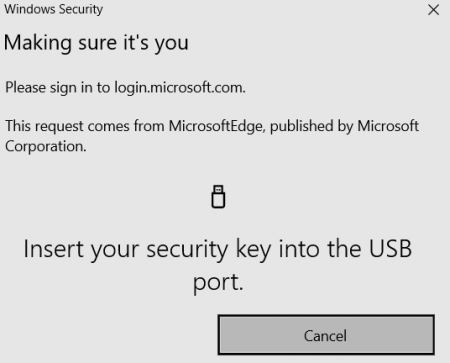
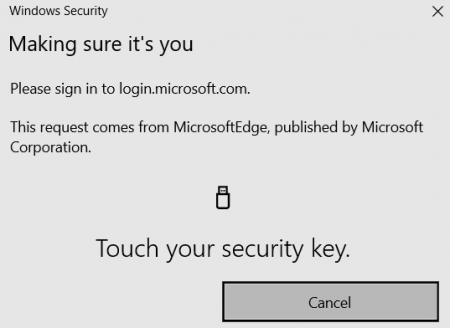
And with that we signed in to our account, without using our username or password!
Login to Windows 10 with a FIDO2 security keys
To login to Windows 10 with a security key, we have to enable this feature first. You can do this in two ways:
- credential provider via Intune
- credential provider via provisioning package
I go for option 1, via Intune
The reason for this is that my device has to be Azure AD joined anyway, and it’s a small effort to do the Intune configuration compared to the provisioning package. It’s also more scalable with Intune
Go to the Azure portal, and search for Intune(or click here for the direct link)
Go to Device configuration -> Profiles -> Create profile And make a profile with the following settings:
Name: [profilename]
Description: [Description of the profile]
Platform: Windows 10 and later
Profile type: Custom
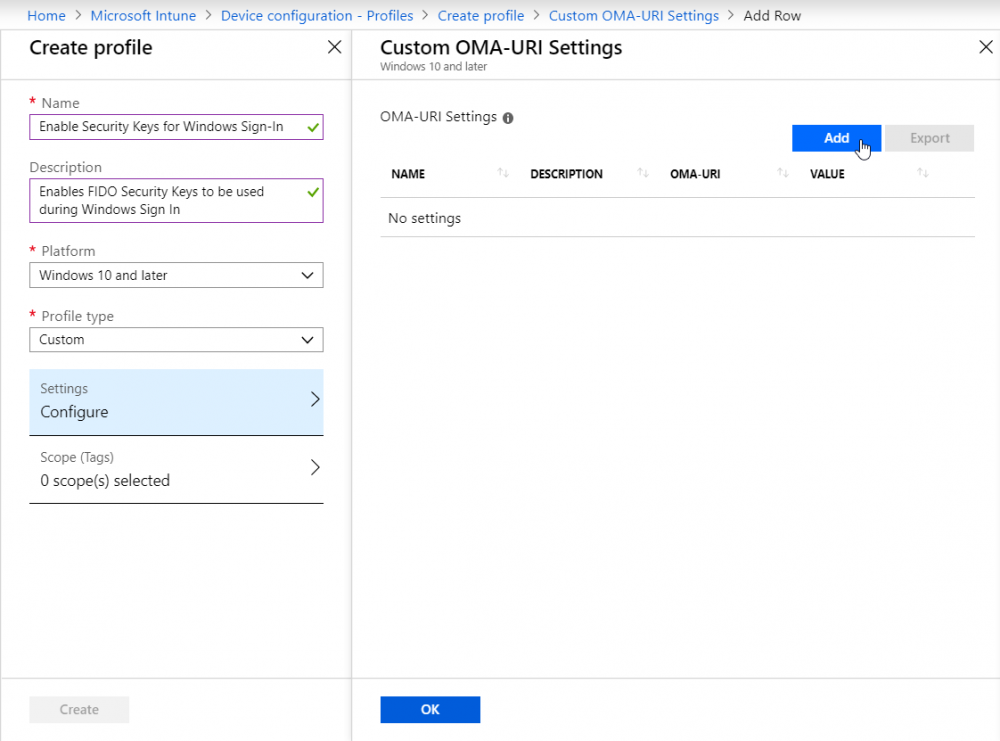
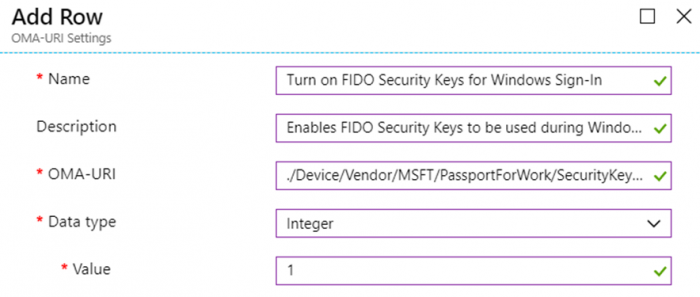
You have to add a new OMA-URI at settings. Click on Add And fill out the following fields:
Name: [Name of the setting]
Description: [Description of the setting]
OMA-URI: ./Device/Vendor/MSFT/PassportForWork/SecurityKey/UseSecurityKeyForSignin
Data type: Integer
Value: 1
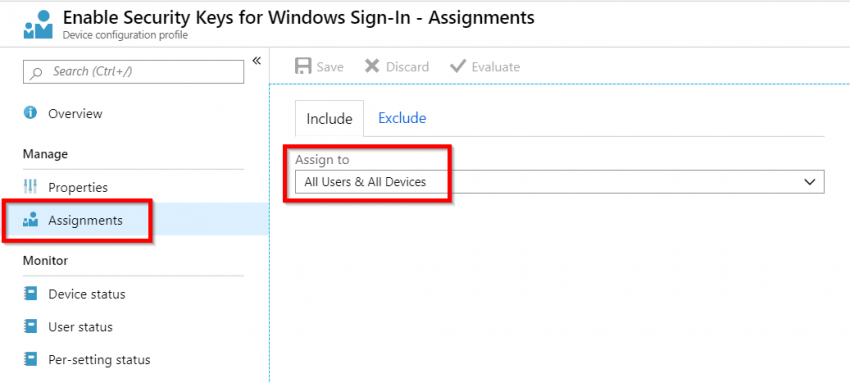
Go to Assignments At Assign to select All Users & All Devices, or optionally select a pilot group or user
As soon as these settings are pushed to our device it’s possible to sign in to windows with our FIDO2 security key For this, click on Sign-in Options, and choose the USB symbol (FIDO security key)
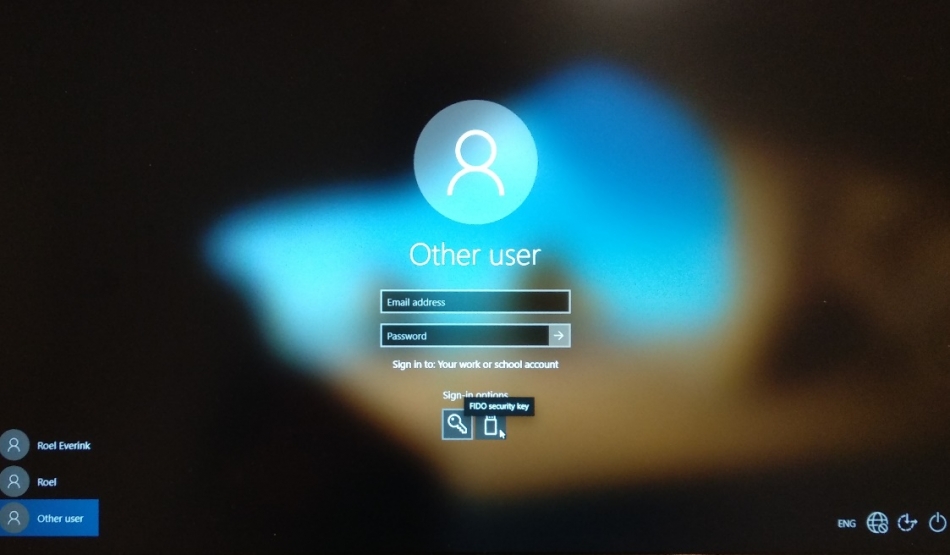
Next we can authenticate on your security key, and we will be signed into Windows, again, without using our username or password!
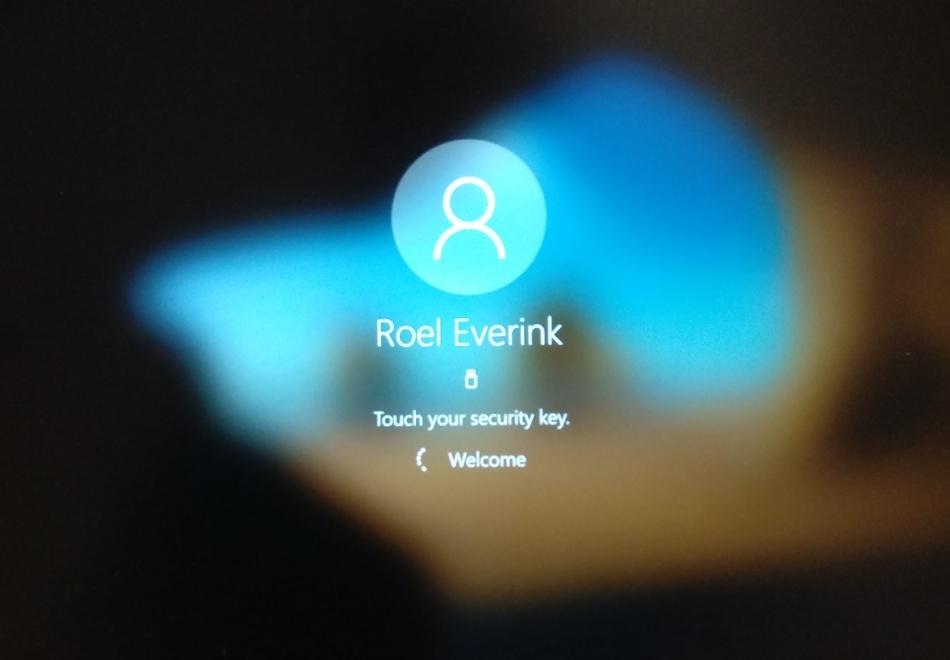
This completes our full setup. We can now sign in to our device and to web pages with our security key and enjoy the benefits of passwordless authentication!
